Digital integrity refers to ensuring that digital data has not been altered, corrupted or manipulated from a given point in time.
This means that the information remains intact, that is, exactly the same as its original state and any modification, even minimal, can be detected.
Digital integrity is achieved through hash functions and there are several software programs that implement hash functions: sha256sum, b3sum, fsum, etc. Regardless of what is used, it is essential to record which algorithm was used in the process, to allow correct verification of data integrity.
The auditor was developed with a focus on digital integrity, implementing an innovation in the calculation of hashes, while bringing useful features not found in the most popular existing software.
Installing the auditor
The auditor is available at: https://thash.org/auditor It must be unzipped to a local folder and, for it to be easily available from anywhere in the prompt, it needs to be copied into a folder included in the operating system's PATH, which are usually:
-
On Windows:
%localappdata%\Microsoft\WindowsApps: (You can paste this shortcut directly into Windows Explorer and it will take you there!),C:\Windows\System32 -
On Linux:
/usr/local/bin/usr/bin,/bin,/usr/sbin
auditor --helpIf you do not have permission to copy to a folder in the PATH, you can use it directly from the folder where it was unzipped. Example: If unzipped to the folder
C:\temp,
type:C:\temp\auditor.exe --help
The auditor implements two subcommands, used in this order:
-
auditor hash pasta: Generates audit files containing the integrity data of files existing in 'folder'; -
auditor check pasta: Uses information from audit files to check whether files in 'folder' are intact.
Usage is detailed below.
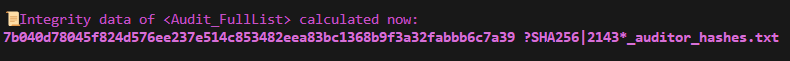 Note: The integrity data is also saved in the file
Note: The integrity data is also saved in the file
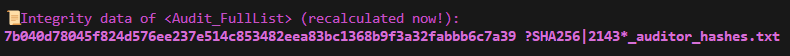 The recalculated integrity data
The recalculated integrity data